Removing weak points from systems and applications is a cybersecurity priority. Companies rely on various techniques to discover software flaws, but no testing method provides a more realistic and well-rounded analysis than a penetration test.
This article is an introduction to penetration testing. Read on to learn how pen testing works and how companies use these tests to prevent expensive and damaging breaches.
Penetration Testing Definition
Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. These tests rely on a mix of tools and techniques real hackers would use to breach a business.
Other common names for penetration testing are white hat attacks and ethical hacking.
Pen testers typically use a mix of automation testing tools and manual practices to simulate an attack. Testers also use penetration tools to scan systems and analyze results. A good penetration testing tool should:
- Be easy to set up and use.
- Be fast at system scanning.
- Sort weaknesses based on severity.
- Automate the verification of weak points.
- Re-verify past exploits.
- Provide detailed reports and logs.
Read our article about the best penetration testing tools and see what experts use to test system resilience.
The main objective of a pen test is to identify security concerns within operating systems, services, applications, configurations, and user behavior. This form of testing enables a team to discover:
- System vulnerabilities and security flaws.
- Lack of compliance with data privacy and security regulations (PCI, HIPAA, GDPR, etc.)
- Lack of security awareness across the team.
- Flaws in the threat identification protocols.
- Room for improvement in the incident response plan.
- Errors in the security policy.
Companies typically hire external contractors to run pen tests. The lack of system knowledge allows a third-party tester to be more thorough and inventive than in-house developers. Some companies also run bounty programs that invite freelancers to hack systems with the promise of a fee if they breach the system.
Penetration testing lies at the core of modern information security risk management approaches, such as Continuous Threat Exposure Management. Find out what Continuous Threat Exposure Management (CTEM) is, how it works, and how it involves penetration testing.
What Is the End Result of a Penetration Test?
The end result of a penetration test is the pen test report. A report informs IT and network system managers about the flaws and exploits the test discovered. A report should also include steps to fix the issues and improve system defenses.
Every pen test report should include:
- An executive summary: The summary offers a high-level overview of the test. Non-technical readers can use the summary to gain insight into the security concerns revealed by the pen test.
- Tools, methods, and vectors: This section covers the tools and methods behind the test. Testers also outline step-by-step attack patterns that led to a successful breach.
- Detailed findings: This section lists all security risks, vulnerabilities, threats, and concerns discovered by the penetration test. Unlike the executive summary, this part of the report goes in-depth into technical details.
- Recommendations: The recommendations section explains how to improve security and protect the system from real cyberattacks.
Learn about the different cybersecurity attack types you can include in your penetration tests.
How Often Should You Run Penetration Tests?
Companies run penetration tests regularly, typically once a year. In addition to annual testing, a company should also organize a pen test whenever the team:
- Adds new network infrastructure.
- Installs new applications.
- Significantly upgrades or modifies infrastructure or applications.
- Sets up an office at a new location.
- Adds new security patches.
- Makes changes to end-user policies.
Depending on your company’s size and budget, running a penetration test whenever the team makes a change may not be realistic. In that case, the team should use a combination of penetration tests and vulnerability scans. While not as efficient, automated vulnerability scans are quicker and cheaper than pen tests.
Understand the difference between vulnerability scanning and penetration testing to create a balanced, well-rounded testing culture.
Penetration Testing Steps
Penetration testing is a complex practice that consists of several phases. Below is a step-by-step look at how a pen test inspects a target system.
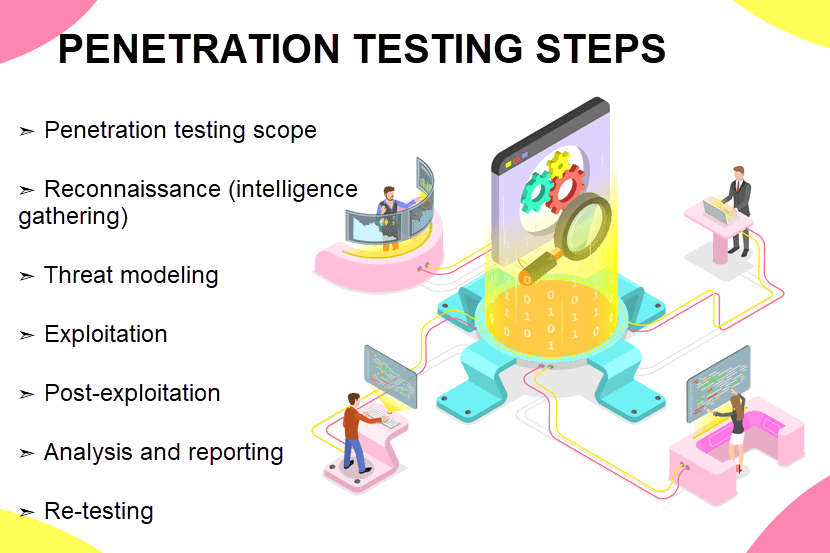
Penetration Testing Scope
This step involves initial preparation for the test. The team should:
- Outline the logistics of the test.
- Define the testing scope.
- Set expectations.
- Set objectives.
- Define the aggression limits of the penetration team.
- Consider potential legal implications.
Reconnaissance (Intelligence Gathering)
Hackers start to learn about the system and look for potential entry points during the intelligence gathering stage. This phase requires the team to primarily gather information about the target, but testers can also discover surface-level weak points.
The reconnaissance step includes the scan of:
- All the hardware.
- The local and wireless networks.
- Firewalls.
- Pertinent applications.
- Websites.
- Cloud-based systems.
- Employee behavior and protocols.
Another common term for the reconnaissance stage is open-source intelligence (OSINT) gathering.
Threat Modeling
Testers use the insights from the reconnaissance phase to design custom threats to penetrate the system. The team also identifies and categorizes different assets for testing.
Exploitation
Testers attempt to break into the target through the entry points they found in earlier stages. If they breach the system, testers attempt to elevate their access privileges. Moving laterally through the system enables pen testers to identify:
- Poor network segmentation setups.
- Access to sensitive data and resources.
- Weak management of accounts and passwords.
Post-Exploitation
Pen testers evaluate the extent of the damage that a hacker could cause by exploiting system weaknesses. The post-exploitation phase also requires the testers to determine how the security team should recover from the test breach.
Analysis, Reporting, and Creating Actionable Steps for Protection
Testers compile the results of the test into a report that outlines:
- The step-by-step breakdown of hacker activity.
- The discovered weak points and vulnerabilities.
- The data testers were able to reach.
- How long the testers remained undetected within the system.
- Steps the company must take to remove vulnerabilities and protect against real attacks.
Re-testing
Once the security team implements the changes from the pen report, the system is ready for re-testing. The testers should run the same simulated attacks to see if the target can now resist the breach attempt.
Standardized Penetration Testing Methodologies
Companies typically rely on one of the five standardized penetration testing methods: OWASP, OSSTMM, ISSAF, PTES, and NIST.
OWASP
The OWASP (Open Web Application Security Project) is a framework for identifying application vulnerabilities. This method allows a team to:
- Recognize vulnerabilities within web and mobile applications.
- Discover flaws within development practices.
The OWASP also enables testers to rate risks, which saves time and helps prioritize issues. This framework has a huge user community, so there is no shortage of OWASP articles, techniques, tools, and technologies.
OSSTMM
The OSSTMM (Open-Source Security Testing Methodology Manual) relies on a scientific methodology for network penetration testing. This peer-reviewed framework provides an accurate characterization of operation security ideal for ethical hacking.
The OSSTMM enables pen testers to run customized tests that fit the organization’s technological and specific needs.
ISSAF
The ISSAF (Information System Security Assessment Framework) provides a specialized and structured approach to testing.
This framework is ideal for testers looking to plan and document every step of the pen test in detail. The ISSAF is also useful for testers using different tools as the method allows you to tie each step to a specific tool.
PTES
The PTES (Penetration Testing Methodologies and Standards) offers a highly structured seven-step approach to testing. This methodology guides testers through all penetration testing steps, from reconnaissance and data gathering to post-exploitation and reporting.
The PTES requires testers to know the organization’s processes to run successful tests.
NIST
The NIST (National Institute of Standards and Technology) offers precise penetration testing guidelines to improve overall cybersecurity. This framework is popular within high-danger industries like banking, communications, and energy.
Complying with the NIST is often a regulatory requirement for American businesses. To comply with the NIST, a company must run penetration testing on applications and networks.
Types of Penetration Testing
Penetration tests differ in terms of goals, conditions, and targets. Depending on the test setup, the company provides the testers varying degrees of information about the system. In some cases, the security team is the one with limited knowledge about the test.
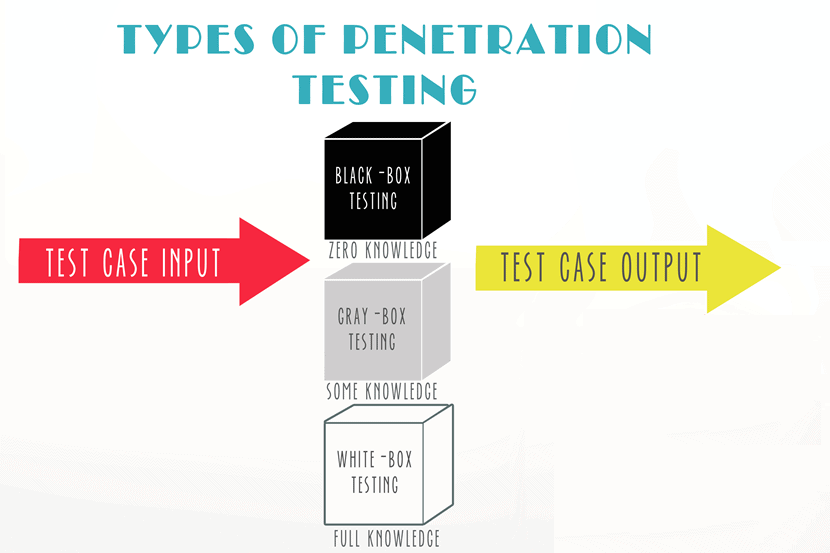
Black Box Penetration Testing
The penetration team has no information about the target system in a black box test. The hackers must find their own way into the system and plan on how to orchestrate a breach.
Typically, the testers only have the name of the company at the start of a black box test. The penetration team must start with detailed reconnaissance, so this form of testing requires considerable time.
Grey Box Penetration Testing
The testing team has the knowledge of a user with elevated privileges. The hacker knows about:
- The design and architecture of documentation.
- Internal structures.
A grey box pen test allows the team to focus on the targets with the greatest risk and value from the start. This type of testing is ideal for mimicking an attacker who has long-term access to the network.
White Box Penetration Testing
Pen testers have information about the target system before they start to work. This information can include:
- IP addresses.
- Network infrastructure schematics.
- User protocols.
- System artifacts (source code, binaries, containers).
Depending on the setup, testers can even have access to the servers running the system. While not as authentic as black box testing, white box is quick and cheap to organize.
Read our in-depth comparison of white and black box testing, the two most common setups for a penetration test.
Targeted Testing
The company’s IT staff and the testing team work together to run targeted testing. Testers and security personnel know each other’s activity at all stages.
Another term for targeted testing is the “lights turned on” approach as the test is transparent to all participants.
External Testing
External testing simulates an attack on externally visible servers or devices. Common targets for external testing are:
- Domain name servers (DNS).
- Web applications.
- Email servers.
- Websites.
- Web and application servers.
- Firewalls.
The objective of external testing is to find out if an outside attacker can break into the system. The secondary objective is to see how far the attacker can get after a breach.
Internal Testing
Internal testing imitates an insider threat coming from behind the firewall. The typical starting point for this test is a user with standard access privileges. The two most common scenarios are:
- A disgruntled employee who decided to damage the system.
- An attacker who accessed the system via a phishing attack.
Internal testing is ideal for determining how much damage a malicious or a compromised employee can do to the system.
Blind Testing
Blind testing simulates a real-life attack. While the security team knows about the test, the staff has limited information about the breach strategy or tester’s activity.
Double-Blind Testing
In a double-blind setup, only one or two individuals within the company know about the upcoming test. Double-blind tests are ideal for examining:
- Security monitoring systems.
- Incident identification protocols.
- Response procedures.
A double-blind test provides an authentic look into the security team’s ability to detect and respond to a real-life attack.
Penetration Testing Approaches (Areas of Testing)
Below are the different penetration testing approaches you can run to examine your company’s defenses.
Network Penetration Testing & Exploitation
Network penetration testing mimics hacking techniques for breaching networks, routers, switches, and hosts.
This form of testing includes:
- Firewall bypassing.
- Evading a next-generation intrusion prevention system (NGIPS).
- Router and proxy server testing.
- IPS and DPS evasion.
- Open port scanning.
- SSH security attacks.
- Testing policies that stop lateral movement.
- Intercepting network traffic.
- Discovering legacy devices and third-party appliances.
This type of testing includes both internal and external network exploitation. Common weak points network penetration discovers are:
- Misconfigured assets.
- Product-specific vulnerabilities.
- Wireless network weaknesses.
- Rogue services.
- Weak password protocols.
A simulated attack on a business’s network infrastructure is the most common type of pen test.
Web Application Security Tests
Application security tests search for potential risks in server-side applications. Typical subjects of these tests are:
- Web applications.
- APIs.
- Connections.
- Frameworks.
- Mobile apps.
Common application vulnerabilities include:
- Cross-site request forgery and scripting.
- Injection flaws.
- Poor session management.
- Insecure direct object references.
- Coding errors.
- Broken authentication or authorization protocols.
- Weak cryptography.
Client-Side or Website & Wireless Network
This type of testing inspects wireless devices and infrastructures for vulnerabilities. A wireless pen test discovers insecure wireless network configurations and poor authentication checks.
This type of testing includes scanning of:
- Web server misconfigurations.
- Anti-malware and DDoS prevention strategies.
- SQL injections.
- MAC address spoofing.
- Media players and content creation software.
- Cross-site scripting.
- Hotspots and access points.
- Encryption protocols.
Social Engineering Attacks
Social engineering tests search for vulnerabilities within employee protocols and behaviors. Falling victim to a social engineering attack can lead to unauthorized access, malware, ransomware, or compromised credentials.
Social engineering pen tests typically mimic real-world attacks such as:
- Eavesdropping.
- Tailgating.
- Phishing attacks.
- Spear-phishing.
- Baiting.
- Scareware.
- Pretexting.
Learn how to prevent social engineering attacks, the most common starting point of a data breach.
Physical Testing
Physical penetration tests attempt to gain physical access to business areas. This sort of testing ensures the integrity of:
- RFID systems.
- Cameras.
- Door entry systems and keypads.
- Employee and vendor behavior.
- Motion and light sensors.
Hackers often combine physical tests with social engineering to create realistic attack conditions.
Cloud Pen Testing
Cloud penetration testing examines the defenses protecting cloud assets. Pen tests identify potential exposures within applications, networks, and configurations in the cloud setup that could give hackers access to:
- Company credentials.
- Internal systems.
- Sensitive data.
This type of testing is essential for companies relying on IaaS, PaaS, and SaaS solutions. Cloud pen testing is also important for ensuring safe cloud deployments.
A Key Part of Any Risk Assessment Strategy
Penetration tests allow a company to proactively discover system weaknesses before hackers get an opportunity to do damage. Run regular simulated attacks on your systems to ensure safe IT operations and prevent costly breaches.



