Introduction
An access control list (ACL) manages user privileges for accessing system locations and resources. While ACLs have their application in personal computing, they are more often utilized in business environments.
In networking, ACLs are regarded as standard network security practices to control network traffic and prevent unauthorized access to database servers, content management systems, etc.
This article will focus on the role of ACLs in networking. It will explain ACL components and common ACL types and provide advice on how best to implement an access control list on a network.
What is ACL (Access Control List)?
An ACL (Access Control List) is a set of rules that allow or deny access to a computer network. The network devices, i.e., routers and switches, apply ACL statements to ingress (inbound) and egress (outbound) network traffic, thereby controlling which traffic may pass through the network.
How Does an ACL Work?
An ACL works as a stateless firewall. While a stateful firewall examines the contents of network packets, a stateless firewall only checks if the packets follow the defined security rules.
ACLs are tables containing access rules found on network interfaces such as routers and switches. When the user creates an ACL on a router or switch, the device becomes a traffic filter.
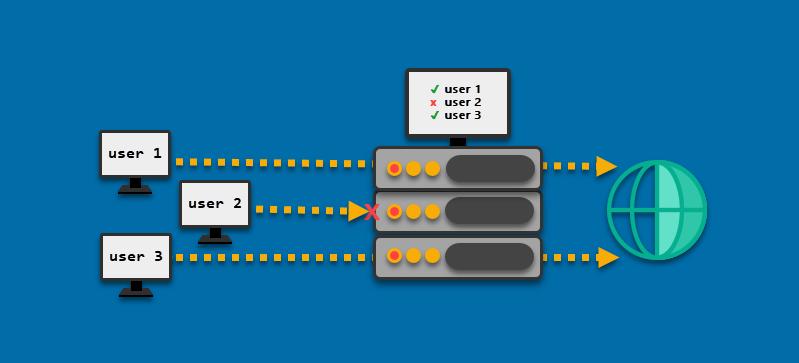
As the diagram above shows, ACLs tell the router whether the traffic coming from a user (IP address) can pass through the device or not.
Numbered and Named ACLs
When creating an access control list, the user can choose to format it as a numbered or a named list.
With numbered access control lists, each list has an identification number:
- Standard access lists take numbers 1-99 and 1300-1999.
- Extended access lists are in the 100-199 and 2000-2699 ranges.
Named access control lists are preferred to numbered lists because names allow network administrators to provide information about the purpose of an ACL.
For example, when setting up an extended ACL that provides rules for the InfoSec office in a company building, the user can create an extended list by entering the following command at the command prompt of the router configuration mode:
access-list extended 120 [rule1] [rule2] [...]While the numbered list created in this way would have the same properties as its named counterpart, creating the named list makes its purpose clearer:
access-list extended INFOSEC [rule1] [rule2] [...]ACL Types
There are five types of ACLs: standard, extended, dynamic, reflexive, and time-based.
The following sections describe each ACL type.
Standard ACL
The basic type of ACL filters traffic based on the source IP address. When a packet attempts to enter or leave the switch, the system checks its IP data against the rules specified in the ACL. The checking process ends as soon as a rule allowing the specific IP address is found.
For example, the following access list number 5 permits hosts on the 192.168.15.0/24 network.
access-list 5 permit 192.168.15.0 0.0.0.255The full syntax for creating a standard ACL is:
access-list list-number-or-name {permit | deny} {source [source-wildcard] | host hostname | any}The source-wildcard parameter is the inverse mask. Calculate inverse masks by subtracting 255 from each subnet mask field. In the example above, 0.0.0.255 is the inverse mask of the 255.255.255.0 subnet mask.
Extended ACL
Unlike standard access control lists, extended ACLs accept rules based on source and destination IP addresses. Furthermore, extended ACL rules may include filtering by protocol type, TCP or UDP ports, etc.
The example below shows an extended access list number 150 that allows all traffic from the 192.168.15.0/24 network to any IPv4 network if the destination has the HTTP port 80 as the host port:
access-list 150 permit tcp 192.168.15.0 0.0.0.255 any eq wwwThe full syntax for the extended ACL is:
access-list access-list-number-or-name {deny | permit} protocol source source-wildcard destination destination-wildcard precedence [precedence] tos [tos] [fragments] time-range [time-range-name] [log]Dynamic ACL
Dynamic ACLs are named extended lists that contain dynamic ACL rules. This ACL type is also known as Lock-and-Key Security.
Dynamic ACLs address the issues arising from the changing of the authorized host's IP address, such as in the case of physically relocating a trusted machine. To confirm identity, the client must enter their username and password. If the validation is successful, the network device alters its access rules to accept the connection from the new IP address.
Reflexive ACL
While a standard ACL does not keep track of the sessions, a reflexive ACL can limit the traffic to the sessions originating from within the host network.
A reflexive ACL cannot be applied directly to the interface - instead, it is usually nested in an extended named access list. This access control type does not support applications that change port numbers during a session, such as FTP clients.
Time-Based ACL
This extended ACL type allows for time-based access control. For example, an organization may allow employees to access certain internet locations only during lunch hours.
Time-based rules are created using the time-range command. The command allows users to set up absolute rules with a single start and end time, and periodic rules, used to set up recurring periods.
ACL Components
The following components make up an access control list:
- The Sequence number identifies the ACL entry.
- The Name provides a descriptive identification for an ACL.
- The Statement is the main part of the ACL. Using statements, the user permits or denies access to an IP address or IP range.
- The Network protocol component allows or denies access to specific network protocols, such as IP, TCP, UDP, etc.
- The Source or destination component defines source or destination IP addresses or ranges.
Some routers allow adding more ACL components, such as:
- Logs, to keep track of ACL events.
- Remarks, to provide space for additional comments about the purpose of the ACL.
Complex ACLs have components for more granular network traffic control based on the ToS (type of service) or DSCP priority.
Benefits of ACL
The primary function of ACLs is to secure the network, but they are also useful for other aspects of network traffic control:
- Block specific users or traffic, allowing for granular access control based on addresses, protocols, traffic types, etc. This property is particularly useful for internet-facing servers.
- Simplify the identification of users and hosts, both local and remote.
- Help congestion avoidance and management.
- Improve network performance by controlling bandwidth to prevent excess network traffic.
- Assist in preventing DoS (Denial of Service) attacks and spoofing.
Note: To provide more robust protection against unwanted traffic in your network, consider using a small server instance to set up a firewall. Small BMC instances are affordable, secure, and well suited for a wide variety of workloads.
How to Implement ACL
The router is the optimal place to apply ACL rules, so knowing the router traffic flow is essential for proper ACL implementation. The concepts of ingress (inbound) and egress (outbound) traffic are essential for understanding network traffic.
The following diagram shows ingress and egress traffic flowing in and out of the network:
- Ingress traffic is the traffic flowing into the router.
- Egress traffic is the traffic that leaves the router.
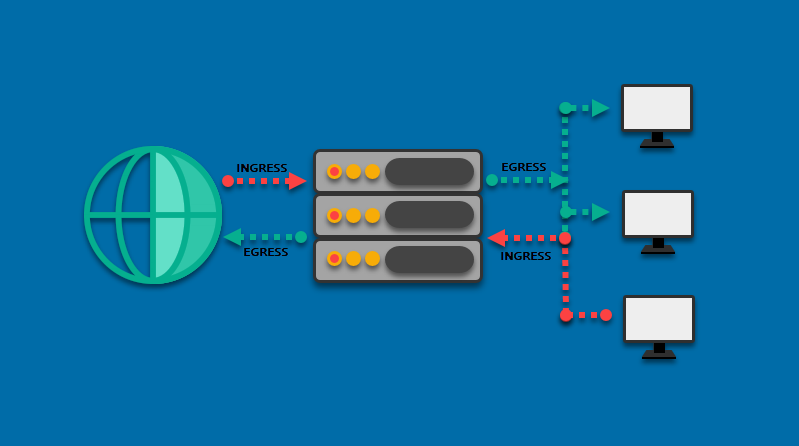
For example, blocking all traffic coming from the internet requires setting up an ingress rule. The source for this rule will be 0.0.0.0, which is a wildcard standing for all the external IP addresses. The destination is the local network’s IP address.
Conversely, blocking internet access for a single machine within a network requires setting up an egress rule, where the source is the machine’s IP address, and the destination is the 0.0.0.0 wildcard.
Below are tips to consider when implementing ACL:
- Create the ACL before applying it on the router or switch. If you start by creating an empty list on a network device, the implicit deny statement included by default may interrupt your network traffic.
- To prevent an ACL from denying all traffic, make sure the ACL contains at least one
permitstatement. - Place more specific rules before the general ones.
- Use an explicit
denystatement. Although each ACL ends with an implicitdenystatement, only explicit statements show when you attempt to display the count of packets denied usingshow access-listcommand. - Use the
remarkcommand whenever possible to provide details about the ACL.
Conclusion
After reading this article, you should be better acquainted with network ACLs, their types, components, and benefits. The article also provided advice for implementing ACL on your network.