Introduction
The easiest way to secure your Kibana dashboard from malicious intruders is to set up an Nginx reverse proxy. By doing so, you ensure only authorized password-protected users can access Kibana (and the data in Elasticsearch).
In this tutorial, you will learn how to configure Nginx reverse proxy for Kibana.

Prerequisites
- A functioning ELK stack installed on your system
- A user account with sudo privileges
- Access to a terminal window/command line
Note: If you still haven’t set up the ELK stack, refer to our guides: Install ELK Stack on CentOS or Install ELK Stack on Ubuntu.
Configure Nginx Reverse Proxy for Kibana
Step 1: Configure Kibana
Before you start setting up Nginx, make sure to edit the configuration files of Kibana and Elasticsearch.
1. First, open Kibana’s configuration file by running:
sudo vim /etc/kibana/kibana.ymlIf you followed the steps outlined in the Kibana installation, the file should be similar to the one displayed below.
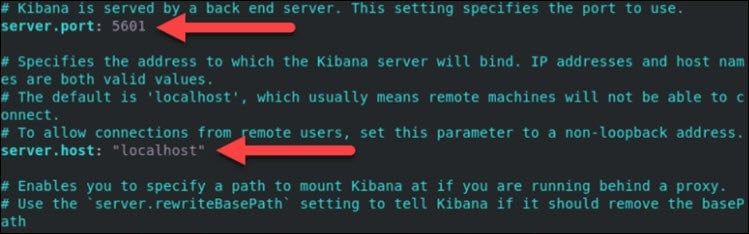
2. Change the default server port and the server host address to the following values:
server.host:"localhost"server.port:56013. Next, save and exit the file.
4. Restart the Kibana service with the command:
sudo service kibana restartStep 2: Configure Elasticsearch
1. Repeat the same process for Elasticsearch. Open its configuration file:
sudo vim /etc/elasticsearch/elasticsearch.yml2. Next, find the following lines and change the default port and host:
http.port: 9200network.host: localhost3. Save the file and restart the service:
sudo service elasticsearch restart4. Finally, verify you can access Kibana by navigating to the following URL in a browser:
http://localhost:5601
Step 3: Install and Configure Nginx
The next step is to set up Nginx.
1. If you haven’t installed Nginx yet, run the command:
sudo apt-get install nginxNote: For more detailed instructions on the Nginx installation, you can refer to How to Install Nginx on Ubuntu 18.04 or How to Install Nginx on CentOS 8.
2. Once you set up Nginx, install the apache2-utils, a utility for creating password-protected accounts:
sudo apt-get install apache2-utils3. Then, create a user account you want to use for accessing Kibana. Replace user_account in the command with the username you want to use:
sudo htpasswd -c /etc/nginx/htpasswd.users user_account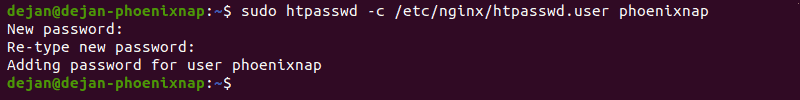
4. The output then asks you to provide and re-type a password for this user:
New password:
Re-type new password:
Adding password for user user_account5. Next, create a configuration file for Nginx:
sudo vim /etc/nginx/conf.d/kibana.conf6. Add the following content once inside the text editor:
worker_processes 1;
events {
worker_connections 1024;
}
http {
upstream elasticsearch {
server 127.0.0.1:9200;
keepalive 15;
}
upstream kibana {
server 127.0.0.1:5601;
keepalive 15;
}
server {
listen 8881;
location / {
auth_basic "Restricted Access";
auth_basic_user_file /etc/nginx/htpasswd.users;
proxy_pass http://elasticsearch;
proxy_redirect off;
proxy_buffering off;
proxy_http_version 1.1;
proxy_set_header Connection "Keep-Alive";
proxy_set_header Proxy-Connection "Keep-Alive";
}
}
server {
listen 8882;
location / {
auth_basic "Restricted Access";
auth_basic_user_file /etc/nginx/htpasswd.users;
proxy_pass http://kibana;
proxy_redirect off;
proxy_buffering off;
proxy_http_version 1.1;
proxy_set_header Connection "Keep-Alive";
proxy_set_header Proxy-Connection "Keep-Alive";
}
}
}7. Save and exit the file.
Note: In the configuration above, Nginx connects to Kibana by listening to port 8882 and Elasticsearch through port 8881. If you used different ports, make sure to alter the configuration accordingly.
Step 4: Restart Services
You need to restart the services for them to recognize the new configuration.
1. Restart Nginx by running:
sudo service nginx restart2. Then, restart the Kibana service with the command:
sudo service kibana restartStep 5: Confirm Authentication Works Properly
1. Open a web browser and navigate to the IP address you assigned to Kibana.
2. An authentication window appears asking you to provide a Username and Password.
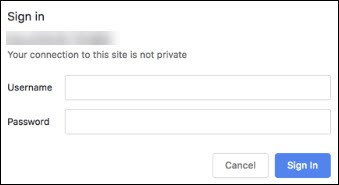
3. Type in the credentials configured while setting up Nginx and select Sign In. If you provided the correct information, the browser opens the Kibana welcome page.

Conclusion
If you followed this guide you should have successfully configured Nginx reverse proxy for Kibana. This provides an additional security layer that protects the data managed through Kibana.
Your next step should be to go through Kibana features used for visualization in our Kibana tutorial.